poverty in saudi arabia, posted with vodpod
“Poverty is an open secret in Saudi Arabia”

|
Firas Buqna posted this photo of himself on Twitter after he was freed from the ZIOCONNED Wahhabi thuggish prisons of the crypto-Zionist Al-Saud....
Lebanese heroes who gave their lives on the altars of the nation also taught us that he who has faith in the nation, in liberty, and in the rights of its citizens will defend them with absolute vigor and most Honorable dedication, and will not fear any threats, threat of oppression, the loss of position or Property, or the disappearance of "Thyself" in a Fiery Syrian/Israeli Car BOMB, with CIA2's Blessing...aiding, abetting, covering-up, re-inventing disinformation to muddy the waters...



poverty in saudi arabia, posted with vodpod

|
Firas Buqna posted this photo of himself on Twitter after he was freed from the ZIOCONNED Wahhabi thuggish prisons of the crypto-Zionist Al-Saud....


According to former head of Afghanistan’s secret service, Amrullah Saleh, “You poison the soil where that grass is, then you eliminate it forever.” This is what has happened on Pakistan’s side of the Durand Line, the Pakistani Taliban from Mohmand (who have relocated to Afghanistan) have poisoned the Pakistani soil by firing upon Afghan forces from points near outpost Salala’s coordinates, in order to bring the two sides together inside Pakistan. This is not the first time that the Pakistani Taliban have used this tactic to bring the Afghan and Pakistani forces together. They used it preceding the “Battle of Wanat” and once again in the “Gora Prai” border post assault. In the Gora Prai video below you can see the individual militants being killed.
The Gora Prai video is from a single Predator; it pales in comparison to the latest assault which allegedly involved repeated runs of aircraft and helicopters, over a period of several hours.
The following was sent to me by a friend from Peshawar. It is self-explanatory.
“Another pack of Lies By NATO
The biggest question is–Why did the joint military commands allow the attack to happen, or make no effort to end it?
If the dust was allowed to settle on this confrontation, then it would surely reveal that it was the TTP bringing Afghan and Pakistani forces into conflict, which they would be inclined to do, considering the level of penetration of the Pakistani Taliban by British, Afghan, and American secret services (SEE: Dissecting the Anti-Pakistan Psyop). Through these separate assets, plus those of India and the Mossad, the Pakistani Taliban have always danced to the same tune as the CIA. This does not necessarily mean that Hakeemullah Mehsud (and Baitullah before him), Faqir Mohammed and Fazlullah are conscious American assets, but that they might as well be. If they are so foolish as to be led around by the nose by spook money, doing the Empire’s bidding, then they are nothing more than petty mercenaries, pretending to be revolutionary jihadis.
This attack can be compared to the Mumbai attack, in that Pakistani jihadis have taken actions which were intended to bring Pakistan into conflict with one of its neighbors. The last time it was India’s turn. Indian leaders kept a cool head, at that time, avoiding another major war with Pakistan, to suit American interests. Will Afghan leaders use their heads, to see this blow-up as their own warning to turn back from the pied piper’s road to oblivion, before it is too late for us all?
by Abdul Moeed Hashmi on 28 November, 2011 –
JALALABAD (PAN): Officials and tribal elders on Monday said the eastern province of Nangarhar was ready for security transition, stressing the need for increasing the strength of Afghan security forces.
Afghan forces will take over the security responsibility in 18 more areas in the second phase of transition. The forces will take full control of Balkh, Daikundi, Takhar, Samangan, Kabul and Nimroz provinces.
The cities included in the second phase of transition include Jalalabad, Chaghcharan, Shiberghan, Faizabad, Ghazni, Maidan Shahr and Qala-i-Naw. Helmand districts Nawa, Nad Ali and Marja are also to change hands.
In Nangarhar, Jalalabad, the provincial capital, Kama, Behsud, Khewa and Surkhrod districts would be handed to Afghan forces. Surkhrod district chief, Syed Ali Akbar Sadat, said they were ready for the handover, but the inadequate police strength posed a problem.
Governor Gul Agha Sherzai had discussed the issue with civil and military officials, his spokesman Ahmad Zia Abdulzai said, adding the provincial capital is ready for the transfer.
“Foreign soldiers disrespect our traditions and we no longer need them,” Wilayat Khan, a tribal elder from Behsud, told Pajhwok Afghan News. The district had only 50 policemen, he said, asking the government to increase their number....

It always amazes me how the world's politicians and media spend most of their energy debating geopolitical prospects that are not going to happen, while ignoring major developments that are happening.
Here is a list of the most important coming non-events that we have been loudly debating and analyzing: Israel is not going to bomb Iran. The euro is not going to disappear. Outside powers are not going to engage in military action inside Syria. The upsurge of worldwide popular unrest is not going to fade away.
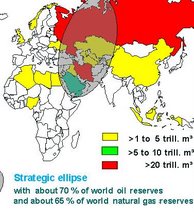
Meanwhile, to minimal serious coverage in the media and on the internet, the Nord Stream was inaugurated in Lubmin on Germany's Baltic Coast on Nov. 8 in the presence of Pres. Medvedev of Russia and the prime ministers of Germany, France, and the Netherlands, plus the director of Gazprom, Russia's gas exporter, and the European Union's Energy Commissioner. This is a geopolitical game-changer, unlike all the widely discussed non-events that are not going to happen.
What is Nord Stream? Very simply, it is a gas pipeline that has been laid in the Baltic Sea, going from Vyborg near St. Petersburg in Russia to Lubmin near the Polish border in Germany without passing through any other country. From Germany, it can proceed to France, the Netherlands, Denmark, Great Britain, and other eager buyers of Russia's gas.
Nord Stream is an arrangement between private enterprises with the blessing of their respective governments. Russia's Gazprom owns 51%, two German companies 31%, and 9% each for one French and one Dutch company. The proportional investments (and the potential profits) are all private.
The key element in this arrangement is that the pipeline does not pass through Poland or any Baltic state or Belorussia or Ukraine. So, all these countries not only lose whatever transit fees they could charge but cannot use their intermediary location to hold up supplies of gas to western Europe while they negotiate deals with Russia.
The German press agency, Deutsche Welle, headlined its story "Nord Stream: A commercial project with a political vision." Le Monde headlined its story "Gazprom is established as a global energy actor." Joseph Bauer, energy expert from Deutsche Bank Research in Frankfurt am Main, opined "It's both a political and a commercial project, and it makes sense on both the economic and political level."
Meanwhile the Russians have told the Chinese that they will not sell them their gas at 30% below the European prices, saying they see no need for Russia to subsidize the Chinese economy. And they have made it clear to Turkmenistan, which has enormous natural gas resources, that they will not appreciate its exporting gas other than via Russia. The Nord Stream launching comes within days of the announcement by the new president of Kyrgyzstan that he expects to close down the U.S. military air base at Manas when its lease expires in 2014. This base has been crucial in U.S. supply links to Afghanistan. Clearly, Russia is strengthening its hold on the Soviet Union's former Central Asian republics.
Both East-Central Europe and the United States are discovering that the scheme to prevent the creation of a Paris-Berlin-Moscow axis is not viable. The European Union's central mechanisms are bending before this reality, as are many of the east-central European countries. This is most difficult for Ukraine, which is torn apart by these developments. And the United States? What in fact can they do about it?